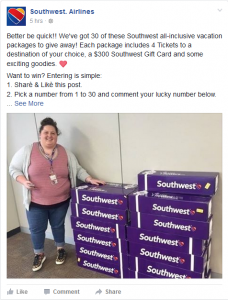
I ran across a fake Southwest Airlines Facebook profile today promising to give away all-inclusive vacation packages to 30 entrants:
(note how the profile name has a period after the first word: “Southwest. Airlines” – that’s how they make it look like Southwest’s own profile page as much as possible)
I hate to see my friends taken in by these fake contests. I don’t know the exact angle for these scams – how do they benefit from creating fake contests except to get many Facebook accounts to “Follow” their fake account?!?
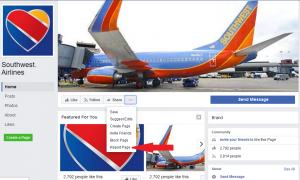
Like a good Facebook citizen, I want to report the fake profile to Facebook so they can review it, determine that it’s fake, and then take it down. Hmmm… how do we do that? Oh, I know. Click on the profile’s page, pull down the “…” option menu, and click on “Report Page”:
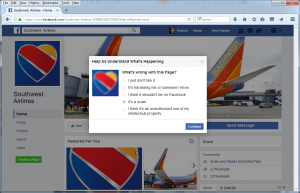
Once I click on Report Page, I’m given several options, including the obvious: “It’s a scam”
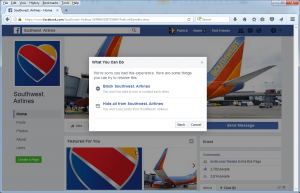
Click on Continue, and I get another list of options:
Two options: “Block Southwest. Airlines” and “Hide all from Southwest. Airlines”. WHAT?!?! Where is “Report to Facebook for review”???
Facebook: Why have you REMOVED the most obvious and most useful option for people to report scams to you??? Instead of letting you review the post or profile directly, you simply want users to stick our heads in the sand and hope the problem goes away. Who gives a shit about our friends and others that might fall victim to this scam, right??
ABSOLUTELY LAME FACEBOOK!!!